How to read legacy FileVault formats on your Mac
When the impossible becomes possible.
Apple
“);});try{$(“div.lazyload_blox_ad”).lazyLoadAd({threshold:0,forceLoad:false,onLoad:false,onComplete:false,timeout:1500,debug:false,xray:false});}catch(exception){console.log(“error loading lazyload_ad “+exception);}});
All good things must come to an end, we’re told, and macOS 10.13 was the very end of the original FileVault, Apple’s file encryption format introduced in OS X Panther 10.3. With the original FileVault, a Mac encrypted a user’s home directory and mounted it as a disk image, more or less. When OS X Lion 10.7.4 appeared, it offered FileVault 2, full disk encryption (FDE), which protects your entire drive by using a special startup procedure at boot time that lets you log in to unlock it. It’s much better than the original directory method, but it required faster Macs to work efficiently enough.
But what about people who, like Macworld reader Alex, had legacy FileVault directories still installed? For many releases, you could use the Security & Privacy system preference pane: click on FileVault and click Turn Off Legacy FileVault. But starting in macOS 10.13 High Sierra, legacy FileVaults no longer work.
The High Sierra installer shouldn’t have let you upgrade if a legacy FileVault remained in place, since it would be unusable. (There was a bug during the beta period that required people with the Sonos app from macOS in order to bypass an error in installation that said a legacy FileVault was installed.)
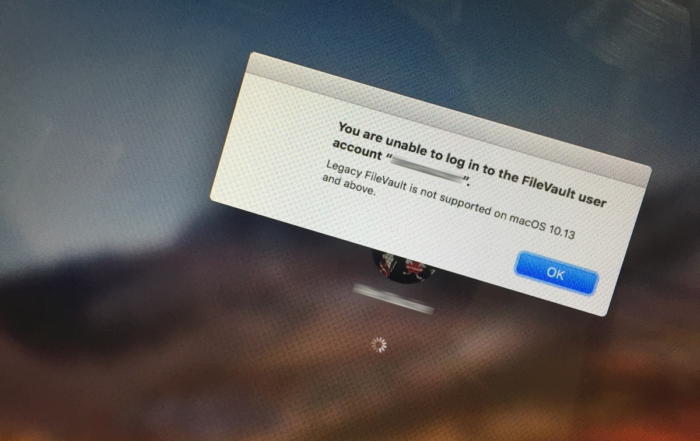
But that happened to Alex. He attempts to log into an account, and is told, “You are unable to log in to the FileVault user account ‘name’. Legacy FileVault is not supported on macOS 10.13 and above.”
 IDG
IDGSomething was askew with a Macworld reader’s legacy FileVault account: it shouldn’t even be possible.
However, when faced with the impossible, we can’t deny it, but try to overcome it. The best course of action is to mount his current computer using Target Disk Mode on another Mac, and attempt to mount the sparse disk image format containing his home directory using his account password. (I can’t test this, because I don’t have an impossible configuration.)
While that won’t restore the account on that Mac, it will allow him to extract any files. He could then either restart on that Mac with another account and create a new account to which he copies the formerly encrypted files or use Recovery to create a new account.
If someone in this situation has a Time Machine backup, it may also be possible to find and retrieve the disk image on the active High Sierra Mac and decrypt that there. Let us know at mac911@macworld.com if you encounter this or find other solutions—it seems like it shouldn’t happen at all.
Ask Mac 911
We’ve compiled a list of the questions we get asked most frequently along with answers and links to columns: read our super FAQ to see if your question is covered. If not, we’re always looking for new problems to solve! Email yours to mac911@macworld.com including screen captures as appropriate, and whether you want your full name used. Every question won’t be answered, we don’t reply to email, and we cannot provide direct troubleshooting advice.


